Keep Servers Running With Infrastructure Tools
Infrastructure, in the context of IT servers, is simply organized server support. It refers to how the servers are physically, logically, and/or functionally grouped together and includes the tools (mostly provided by vendors and occasionally custom-made by the system...
IT Efficiency Through Converged Infrastructure
The idea of converged infrastructure revolves around forming a single optimized IT package by putting together several components to meet present-day business needs. According to HP, converged infrastructure meets these needs “by bringing storage, servers, networking,...Systems Can Be Attacked Via NTP Flaws
At least three serious vulnerabilities in the Network Time Protocol (NTP) have been uncovered by security researchers at Google in 2014. This is quite serious because of the sheer number of computers that may potentially be targets of DDoS (click here to read earlier...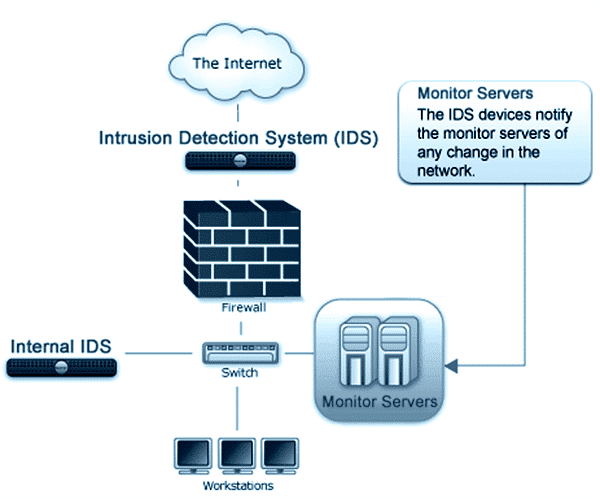
Who Needs an Intrusion Detection System?
Intrusion detection systems (also called ID systems and IDS) have been, and are still constantly being developed in response to past and present attacks on many high-profile websites and networks, including those of Sony, eBay, Yahoo Mail, Google, Apple iCloud, UPS,...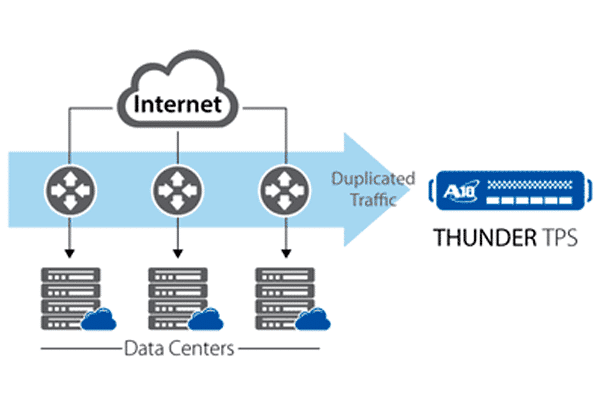
Here Comes the Anti-DDoS Appliance
“More creative and varied”, this is how Brad Casemore describes the current nature of DDoS attacks in a recent article in the TechTarget website. Casemore, who is research director at International Data Corporation (IDC), said that the burden is on the...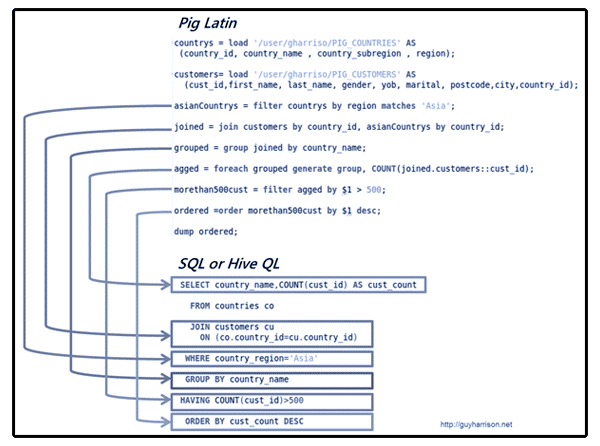
Big Data Analytics with Apache Hive
A few posts back, we encountered the evolving term big data which describes gigantic mass of data that big business enterprises are eyeing to mine for whatever value can be obtained from the data. Examples of big data may be found in the unimaginable collection of...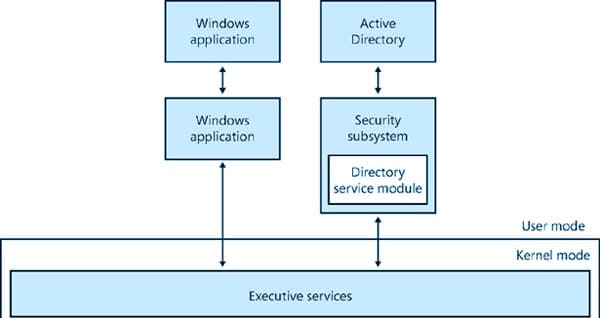
Did Cisco Migrate to Active Directory?
Yes. Cisco Systems, the dominant giant in the networking equipment industry, migrated to Active Directory. But before we look into the why or how of this story, let’s have a little background on Active Directory and on Cisco. Active Directory Active Directory (AD),...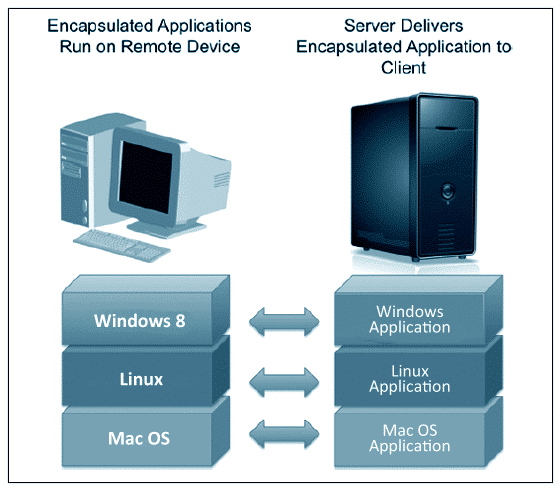
Benefits of Application Virtualization
Many layers of virtualization are currently at work, and one of them is application virtualization. Application virtualization is software technology that implements the encapsulation of an application so that it can be isolated from its host OS. The resulting...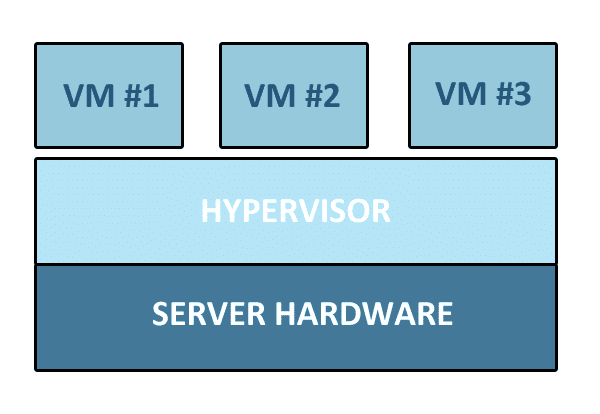

 Server deployment
Server deployment Server support
Server support Extended server support
Extended server support Managed servers
Managed servers