DIY Routines to Keep Your Linux Server in Top Condition
Does your network run mainly on a Linux server? Just like any other network server, your Linux system needs to be checked regularly to keep it in good shape. There are a few things you may be able to do without having to call for outside help. One of the most...Keep Servers Running With Infrastructure Tools
Infrastructure, in the context of IT servers, is simply organized server support. It refers to how the servers are physically, logically, and/or functionally grouped together and includes the tools (mostly provided by vendors and occasionally custom-made by the system...
IT Efficiency Through Converged Infrastructure
The idea of converged infrastructure revolves around forming a single optimized IT package by putting together several components to meet present-day business needs. According to HP, converged infrastructure meets these needs “by bringing storage, servers, networking,...Systems Can Be Attacked Via NTP Flaws
At least three serious vulnerabilities in the Network Time Protocol (NTP) have been uncovered by security researchers at Google in 2014. This is quite serious because of the sheer number of computers that may potentially be targets of DDoS (click here to read earlier...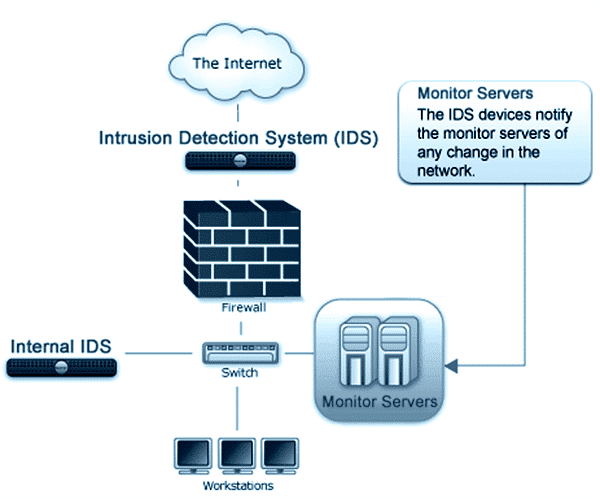

 Server deployment
Server deployment Server support
Server support Extended server support
Extended server support Managed servers
Managed servers